BruCON 2025 – Beer, Waffles, and a Product Review Cabal
My Conference Review
I spent a couple of excellent days at BruCON in Belgium. It’s a conference that blends deep technical content with a relaxed friendly hacker vibe all fueled by local Belgium beer, Club Mate and waffles. My wife and I turned the trip into a broader European vacation, with stops in France, the Netherlands, and Luxembourg, but I want to focus this post on BruCON itself - and why it should be on your list of conferences to attend.
Getting to BruCON
First, I have to give a big shoutout to Rita, our speaker wrangler. My friend, Matt Virus and I met her at NoHat 2024 (another security conference I highly recommend) and she was adamant that our talk would be great fit for BruCON.
Matt and I submitted and were accepted for a session titled:
Our Time in a Product Review Cabal: And all the malware and bugs that came with it
It was a similar talk to what we had previously presented at ShmooCon and NoHat, but this year we expanded the scope using a $200k AI server to examine firmware and updated the presentation with fresh findings.
Conference Location: Mechelen and Lamot

BruCON takes place in Mechelen, a charming Belgian city tucked between Brussels and Antwerp. It’s smaller and calmer than either of those cities, but that’s part of its appeal. The cobblestone streets, canals, and open squares make it easy to explore on foot, and there’s no shortage of shops and cafés. There’s something about Mechelen’s laid back pace that clicks perfectly with the BruCON hacker vibe: curious and approachable.
The conference itself is hosted at Lamot Mechelen (Van Beethovenstraat 8–10, 2800 Mechelen), a beautifully converted brewery turned event space right on the Dyle River. The venue mixes old industrial with modern design, giving the talks and workshops a unique energy, equal parts historic and cutting-edge tech. You can walk from one room to another and catch views of the river through glass walls, enjoy the atmospheric lighting[1], or stop at the bar for a Belgium beer. It's one of those spaces that makes you feel both energized and inspired, which is exactly what you want from a conference like BruCON.



Con Highlights
Beyond the technical talks, BruCON had some standout areas that I wanted to highlight in my review. The Maker Space was particularly fun. This is where I had my first Club Mate, which apparently is a staple in the hacker and maker community. The caffeine and carbonation definitely keep you going through long conference days. The maker space itself was busy with activity, full of people sharing what they were working on and talking about different building activities - from addressable LEDs to Teletext monitors. The maker space team, ran by Ko-Lab, also had their hand in several CTF challenges, including a fun one where I had to go search a nearby boat dock for a "drop-site", which was broadcast in a repeated signal with surreptitious radios spread through the con.
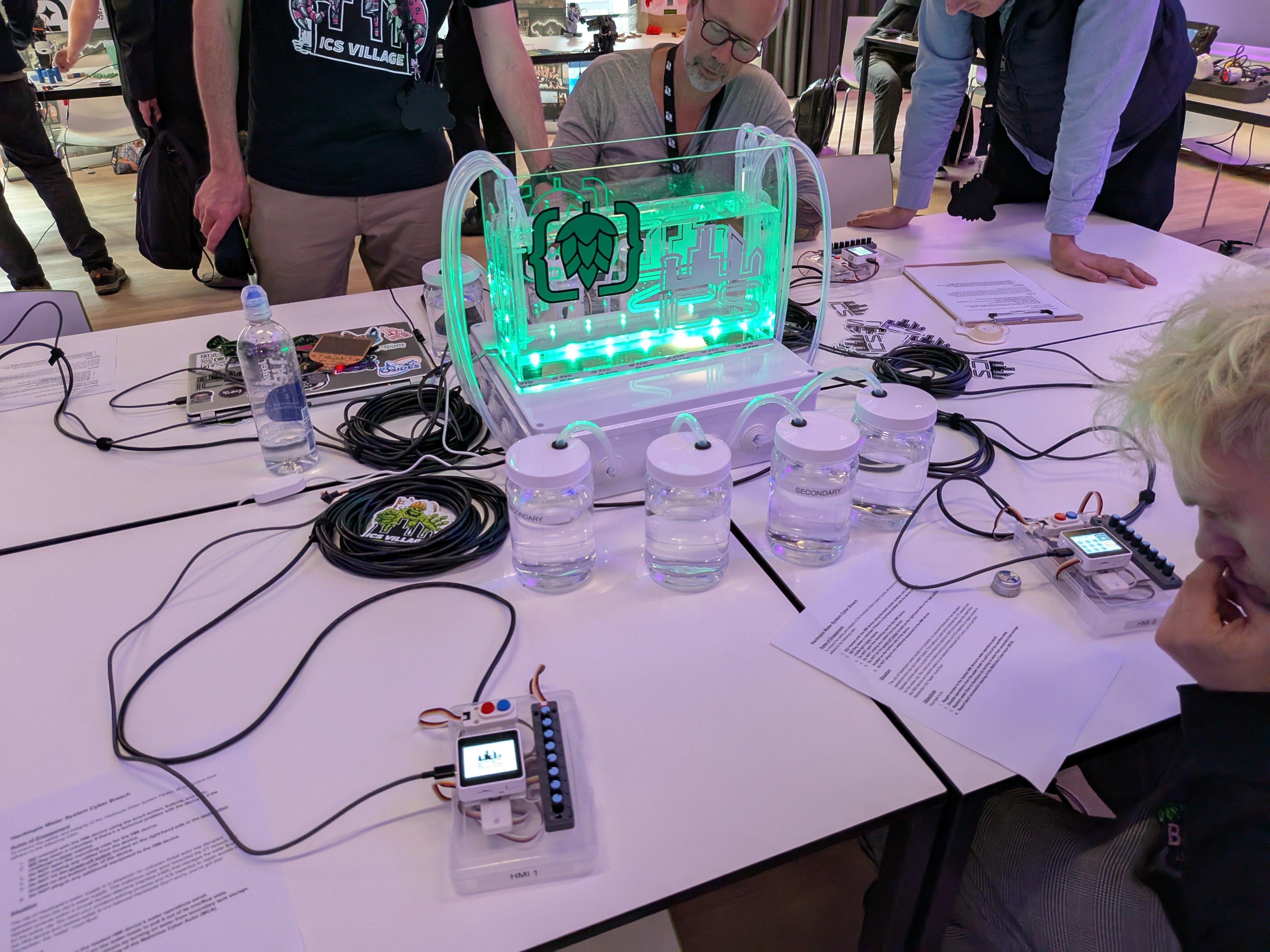
The IOT/ICS (Industrial Control Systems) and Robotics Villages were equally impressive. They had a full robot demonstration[2], a robotic hand that you could interact with, and—most interestingly—a mock water pump station set up specifically for hacking. It's one thing to read about ICS security in papers or talks, but seeing a physical station setup where you can actually explore attack vectors and defensive measures brings the whole field to life. The hands-on nature of these areas really embodies what makes BruCON special: it's not just about consuming information, it's about engaging with it.


And of course, there was a conference CTF, which I always enjoy competing in. I entered and managed to achieve 22nd place with about a day of focused effort. The challenges were well-designed, mixing quick wins to get momentum, then ramping up to more complex problems. I talked about my favorite challenge in the Maker Space, but I equally enjoyed the web and misc categories. Because Matt and I were busy exploring and prepping for our talk, I didn't get to participate in all of the events I would've liked, including the RFID CTF from Vinnie Vanhoecke's Pentahub, which sounded very educational.
Our talk
Our talk was titled "Our time in a Product Review Cabal", a play on the group of friends we started doing reviews of free products with. It all started during the pandemic when Matt received a postcard promising a free gift with an online retailer review. We shared how we managed to get free packages nearly every day, but there's a catch: most of the products arrived with malware, backdoors, or glaring vulnerabilities.
Next, we walked through a subset of these vulnerable products, covering how to detect issues and mitigate them. From cameras to light switches, routers to vacuum cleaners, the product list was expansive. There's nothing these vendors won't copy, and nothing they won't offer up. The story makes for a good conversation starter, but we dove deep into the tear-down and technical analysis. It's a blend of social engineering, hardware hackery, and software vulnerabilities, we truly felt like this talk had something for everyone.
The talk was well received and we fielded some questions we had never received before, such as "Did you try to work with the vendors to fix the vulnerabilities?" and "Do you have a list of tools required to get started with this kind of research?". Matt and I explained that we believed the vendors to be disingenuous already (given they were paying for reviews), so we hadn't followed up with them - assuming bad intent. It was a thought-provoking question that gave us something to think and talk about post-con. Matt also addressed the tool list in a blog post he made on hackspace.io.
See our video and slides below
Final Thoughts
BruCON reminds me why I love security conferences in the first place. The mix of nerdy discussions, hallway conversations, and genuine community made it one of the most rewarding events I've attended in 2025. The talks were deeply technical, but the atmosphere was approachable and collaborative.
If you get the chance to attend or speak at BruCON, take it. You'll leave with new ideas, new friends, and probably a few stories best shared around a Belgium beer.
Links and thanks
- BruCON: brucon.org
- Rita, our speaker wrangler
- Big thanks to the organizers, volunteers, and everyone who came to the talk.
If you were there and want demos or to chat, ping me - happy to collab.
Other Trip Highlights
While BruCON was the main event, Matt and I also visited the crown jewels at the Lourve.
Yes, @themattvirus and I visited the Louvre on our trip to @brucon. Yes, we cased the jewels, and noted that their cameras were obsolete [1] for our talk, but no, we did not steal them.
— Adam Schaal (@clevernyyyy) October 23, 2025
[1] https://t.co/znPlXkexm9 pic.twitter.com/5tvhnJ8Ore